






SSH (Secure Shell) is a network protocol that allows secure remote access and control of computer systems. It provides a secure channel over an unsecured network, greatly enhancing the security of remote connections. SSH remote connection has become an essential tool for system administrators, developers, and network engineers, enabling them to manage and administer servers and devices remotely. This article will explore the power of SSH remote connection, its benefits, and how it can be harnessed effectively.
We have a piece of special news for Linux users, and that is that if you want to buy a Linux VPS server, you can use quality plans with excellent performance and immediate delivery.
SSH remote connection is a cryptographic network protocol that enables secure access to remote systems. It also provides authentication, encryption, and integrity of data transmitted over the network.
SSH operates on the client-server model, with client software initiating the connection to the remote server. It should be noted that SSH utilizes public-key cryptography to authenticate the client and establish a secure connection.
– Enhanced Security: SSH encrypts all data, including passwords, preventing eavesdropping and unauthorized access.
– Remote Administration: SSH allows system administrators to manage servers and devices remotely, reducing the need for physical access.
– File Transfer: SSH provides secure file transfer capabilities, allowing users to securely transfer files between systems.
– Tunneling: SSH facilitates the creation of secure tunnels, enabling secure access to services running on remote systems.
A) Setting up SSH
– Install SSH server software on the remote system, ensuring proper configuration and security practices.
– Generate SSH key pairs for clients to establish secure connections.
– Disable password-based authentication and enforce key-based authentication for added security.
B) Securely Accessing Remote Systems
– Open an SSH client on the local system and connect to the remote server using its IP address or hostname.
– Provide the necessary credentials (private key and passphrase) for authentication.
– Once connected, the user gains access to the remote system’s command-line interface or can execute specific commands remotely.
C) Advanced Usage
– Utilize SSH port forwarding for securely accessing services or applications running on remote systems.
– Employ SSH agent forwarding to enable authentication without storing private keys on intermediate systems.
– Utilize SSH-based VPN (Virtual Private Network) for secure and encrypted communication between networks.
To enable SSH in Windows, just follow the following path:
– First, search for Settings and open it.
– Then click on Apps & features in the left column.
– On the right side, click Optional features:
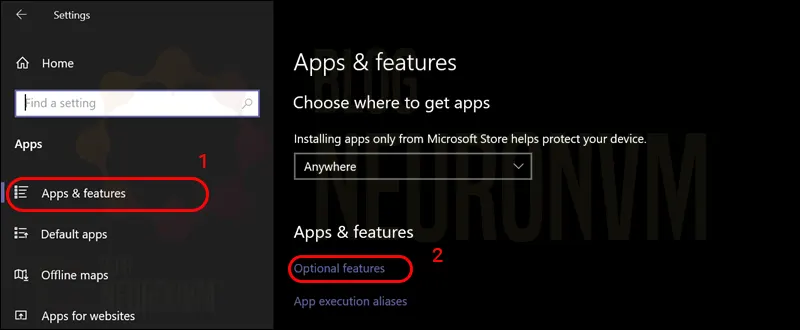
Now it’s time to click Add a feature:
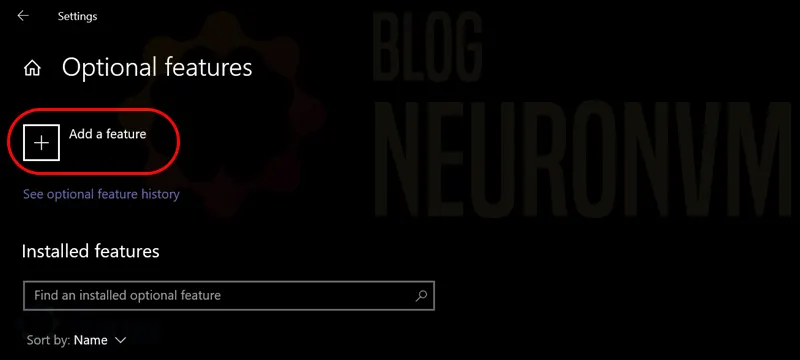
Type OpenSSH in the search field and install it when it appears:
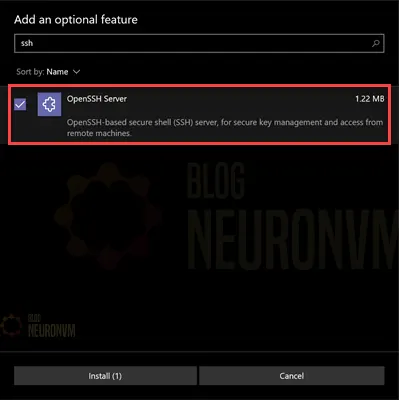
On Debian/Ubuntu:
To install the OpenSSH client component in Ubuntu and Debian, you can run the following command:
sudo apt install openssh-client
On CentOS/Fedora:
Also, to install the OpenSSH client component in CentOS and Fedora, you can run the following command:
sudo dnf install openssh-clients
sudo yum install openssh-clients
On Debian/Ubuntu:
To install the OpenSSH Server component in Ubuntu and Debian, you can run the following command:
sudo apt install openssh-server
On CentOS/Fedora:
Also, to install the OpenSSH Server component in CentOS and Fedora, you can run the following command:
sudo dnf install openssh-server
sudo yum install openssh-server
Finally, start and enable SSH by running the following commands:
sudo systemctl start sshd
sudo systemctl enable sshd
SH remote connection is a powerful tool that brings numerous benefits to individuals and organizations. It provides a secure means of accessing and managing remote systems, enhancing both convenience and security. By harnessing SSH effectively, users can administer servers, transfer files securely, and create encrypted tunnels for accessing services. When properly configured and employed, SSH remote connection becomes an indispensable asset for system administrators, developers, and network engineers, empowering them to perform their tasks efficiently and securely in today’s interconnected world.
How useful was this post?
Click on a star to rate it!
Average rating 3.2 / 5. Vote count: 22
No votes so far! Be the first to rate this post.
 Tags
Tags
Most likely, you are already familiar with the node.js platform. This platform is provided as an ope...



 Tags
Tags

In this article, we are going to explain to you Why You Should Move to a More Powerful Dedicated Ser...



 Tags
Tags
What is your opinion about this Blog?








