






If you are looking for a popular operating system that is useful in security positions and for computer forensic experts, you should turn your attention to Kali Linux. This operating system has many features that are very important in the field of cyber security. This article is presented for exploring the features of Kali Linux and will try to give a comprehensive overview of that.
Kali Linux is an open-source Linux distribution that is based on Debian and introduced in 2013. The Kali Linux operating system is a powerful tool developed to perform tasks such as ethical hacking and manipulation of network tools. The most important advantage of this system is that it is free. To install and run Kali Linux, we recommend you use our high-speed and high-quality Linux VPS servers.
The perception of penetration testing has changed over the years. Kali Linux is also a penetration testing tool and is one of the systems that comes with many features. These features are as follows:
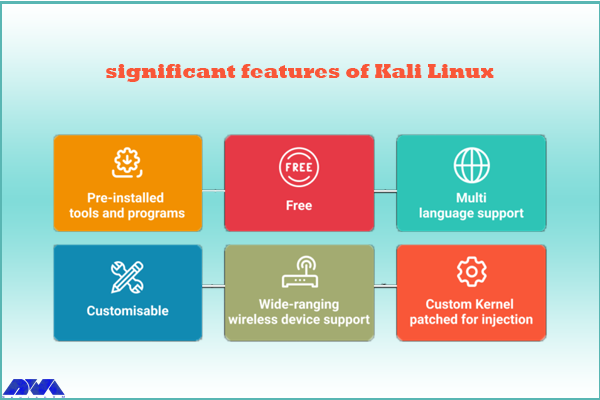
– Kali Linux contains more than 600 penetration testing tools like Burn Suite, Nmap, Wireshark, Air crack-ng, Metasploit framework, John the Ripper, and so on. These are practical tools for penetration testing and hacking.
– Kali Linux is provided free and open-source.
– It is capable of supporting various USB and wireless devices and interfaces.
– Packages and repositories in Kali Linux are GPG signed.
– Filesystem Hierarchy Standard (FHS) is maintained in Kali Linux.
– It supports multiple languages.
– The users can customize Kali Linux appearance as their choice cause it is completely customizable.
– It supports MRMEL and ARMHF which makes it available on a wide range of ARM devices like Raspberry Pi.
– Another prominent feature of Kali is that it supports accessibility features for visually impaired users with voice feedback and braille hardware support.
– There is regular customization and patching of the kernel for any vulnerability in Kali Linux.
– Live Boot system is supported by Kali Linux using a USB device without any touching of the host operating system.
– ISOs are customizable on Kali Linux. Every security researcher has their own needs. Users can produce a custom-optimized ISO file with a selected set of meta-packages.
– Kali is equipped with an encryption mechanism for persistent volume(s). This way, The saved files are able to be secured using Luks Nuck containers.
– You can use Kali from the Windows Subsystem for Linux or WSL. Use Win-Kex for this reason.
– Kali NetHunther is a free, open-source Android application and is useful for common attacks such as Bluetooth attacks or USB HID attacks, and so on.
– Another feature is Kali Undercover. You can blend the appearance of Kali with Windows OS. So, if you activate the Kali Undercover feature, the menu and your desktop will look like Windows OS.
– Kali is able to support any platform. You can run Kali on ARM, Bare Metal, Cloud, Containers like Ducker and Alsovirtual box, and VMware.
– This operating system is a little bit complicated and is not beginners friendly.
– If you run this system from a virtual machine, It’s possible that all the hacking tools do not work properly.
– A lot of junk space is taken by Kali.
Kali Linux is one of the most advanced operating systems for penetration testing and as mentioned in this article, it contains more than 600 tools such as Nmap and Wireshark. It is mainly used for advanced penetration testing and security auditing. we recommended this platform to professionals and advanced users because it is not beginners friendly. Read this content to get more familiar with the greater features of Kali Linux. If you have any questions, leave a comment here.
Game developers don’t focus on Linux because it contains just 2% of the users. As a result, It is not designed for hardcore gaming and Kali is not either.
You can setup Kali as your basic secure shell server with no desktop with 128 MB RAM but note that 512 is recommended. Also, 2 GB of disk space is needed.
How useful was this post?
Click on a star to rate it!
Average rating 0 / 5. Vote count: 0
No votes so far! Be the first to rate this post.
 Tags
Tags
Nowadays, JavaScript is present in different places, and various things are done with it. Although J...



 Tags
Tags

Every year, breaches of users' information and privacy cause huge financial and credit losses t...



 Tags
Tags
What is your opinion about this Blog?








