






You can use SkipFish for web application security scanning, which helps identify vulnerabilities and security issues in web applications. This open-source tool was developed by Google and is designed to evaluate the security status of web applications by performing various tests and scans. We will focus on SkipFish and will try to help you figure out how to install SkipFish on Kali Linux. So read this article carefully to get the best scanner for scanning web applications.
SkipFish is a type of penetration testing tool that works automatically. It is open-source and was created on GitHub for security researchers. You can use this tool to collect information and test the security of websites, VPS, Admin RDP, and dedicated servers.
SkipFish has a simple structure and is one of the best penetration testing tools. This tool can target many integrated tools for testing in the target system. SkipFish can also be used to detect the security of active web applications. It can be used by security professionals, developers, and system administrators to identify potential weaknesses in web applications before they are exploited by attackers.
In the next section, you will find out some significant and practical features of SkipFish:
Let’s start the installation process using the step-by-step instructions here:
The first step to installing the SkipFish tool is moving to the desktop and then typing the command below:
git clone https://gitlab.com/kalilinux/packages/skipfish.git
Now SkipFish will be installed in your Kalli Linux system.
As the second step, you should move SkipFish into the tool directory with the following command:
cd skipfish
ls
skipfish -h
At last, you will be able to see the tool’s help menu that is now active. You can use all of the flags with the tool. As soon as you download the tool, you can learn how to utilize it.
Tip: Most of the time you don’t need to install SkipFish because it comes pre-installed in Kali Linux.
After the installation part, You can type the command below in the terminal to check its option:
sudo skipfish -h
We will show the usage of SkipFish with some examples.
Example 1: Use the SkipFish tool for scanning a WordPress website with the help of an IP address:
skipfish -o 202 http://192.168.1.***/wordpress
You can see the tool’s report here:
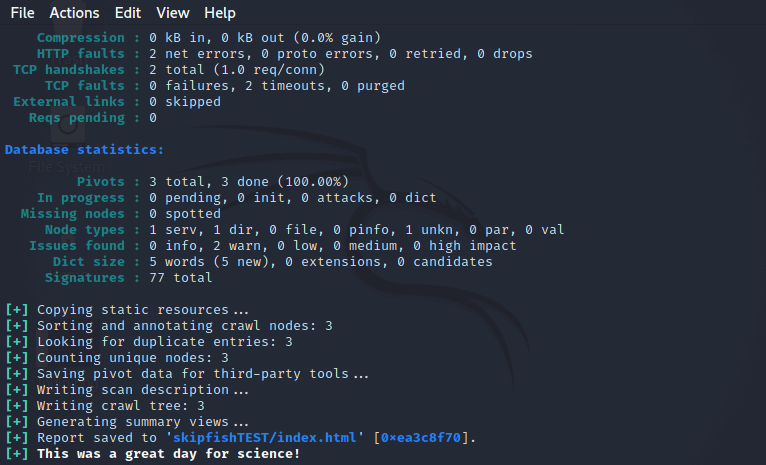
Example 2: You can scan bodegeit with the following command:
sudo skipfish -o Skipfish http://192.168.***.37/bodegeit
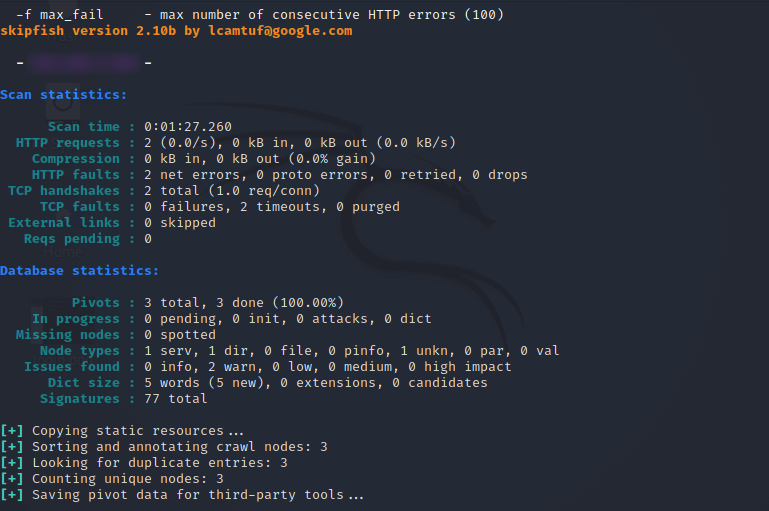
As a result, you can view all relevant data such as data, scan time, HTTP requests to hosts, HTTP errors, etc.
SkipFish is a command line tool that can be run on different operating systems. To configure the scanning process, it needs to specify the target URL and various options. The generated report can be viewed in the browser to understand the security findings. The way this tool works is that it works using dictionary-based crawlers and recursive crawling and creates a map in the console of the site in question.
With the help of this tool, you can have all active security checks in the domain. Finally, SkipFish produces a report that can be further used for security assessments.
Note that security scanning tools like SkipFish are only part of a comprehensive security strategy. Regular manual security tests, code reviews, and other security measures are necessary to ensure the overall security of web applications.
SkipFish is now installed on your Kali Linux system and ready to be used. As we mentioned above, SkipFish is a web application security scanner, so make sure to use it responsibly and only on systems and applications you have permission to scan. Please note that software and repositories may change over time, so it’s best to refer to the official SkipFish repository or documentation for any updates or changes. Happy coding!
How useful was this post?
Click on a star to rate it!
Average rating 0 / 5. Vote count: 0
No votes so far! Be the first to rate this post.
 Tags
Tags

If you are looking for a popular operating system that is useful in security positions and for compu...



 Tags
Tags
Nowadays, JavaScript is present in different places, and various things are done with it. Although J...



 Tags
Tags
What is your opinion about this Blog?








