






OpenSSL is one of the most widely used tools in the field of SSL. Since the launch of the ”HTTPS Everywhere” campaign, the landscape of encryption has changed dramatically. If you do not use an SSL certificate, popular browsers such as Chrome and Firefox will not consider your site as a “secure” website. Therefore, this article will teach you How to Setup OpenSSL on RDP 2016 Server.
Prerequisites
– An Admin RDP with Windows Server 2016 with administrative access.
– Ensure that the Visual C++ Redistributable for Visual Studio 2015 is installed on the server.
– Download the latest version of OpenSSL for Windows from the official website.
1. The OpenSSL library code is available from the official GitHub repository.
2. OpenSSL Tools is a collection of shell scripts for easier use of OpenSSL.
3. SSL Checker can help you diagnose problems with OpenSSL installation. Just enter the domain name.
4. The OpenSSL CSR tool can generate a CSR based on your input parameters.
5. Win32 OpenSSL is a distribution of OpenSSL that can be easily installed on Windows devices.
You must first go to the OpenSSL download page and download OpenSSL, which is compatible with your device’s CPU architecture:
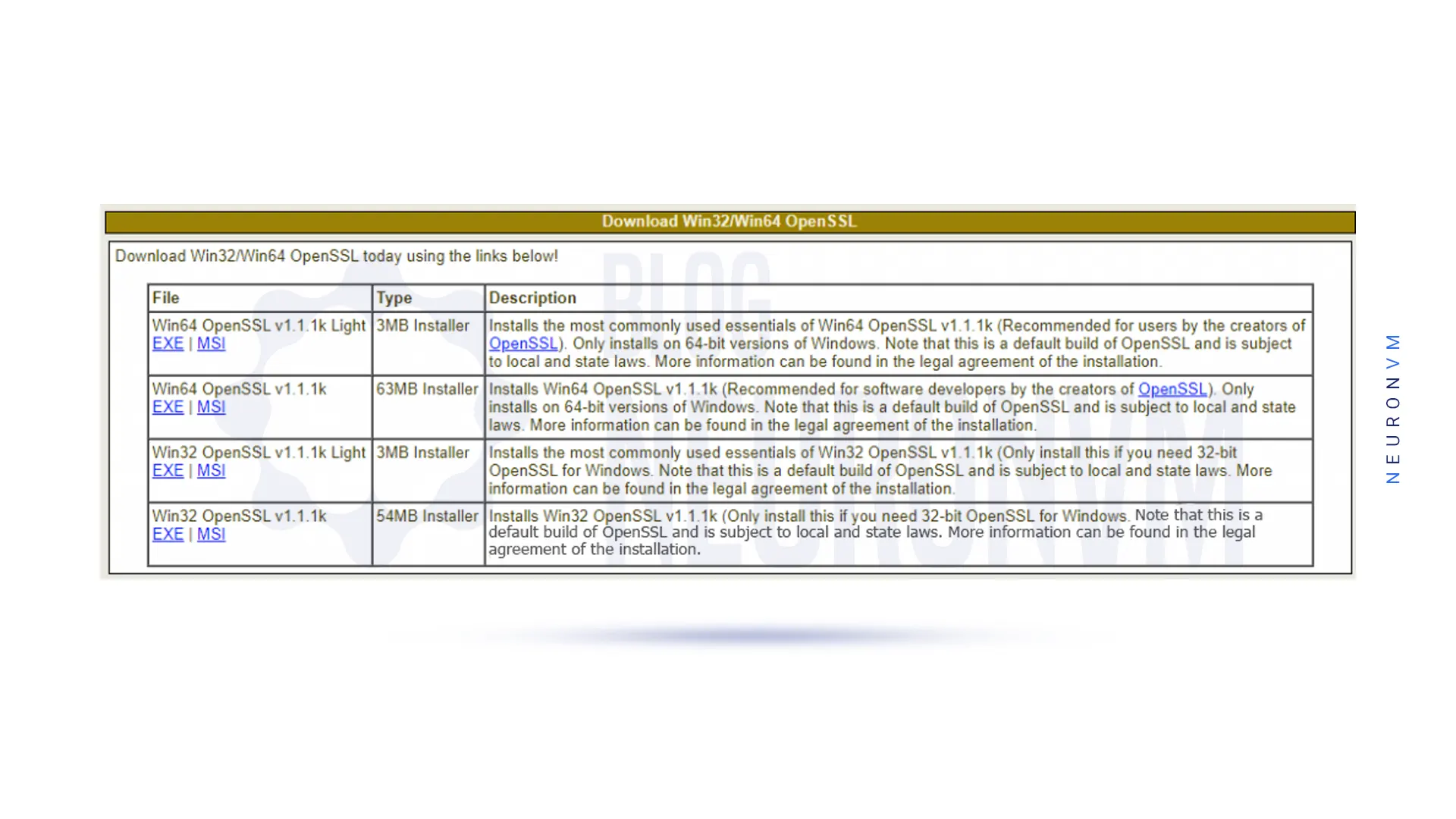
You can also download OpenSSL by running the following command:
curl.exe -L -o Win64OpenSSL.exe https://slproweb.com/download/Win64OpenSSL-1_1_0j.exe
Now that you have successfully downloaded OpenSSL, we need to install it. To do this, you must run the installer through PowerShell:
.\Win64OpenSSL.exe
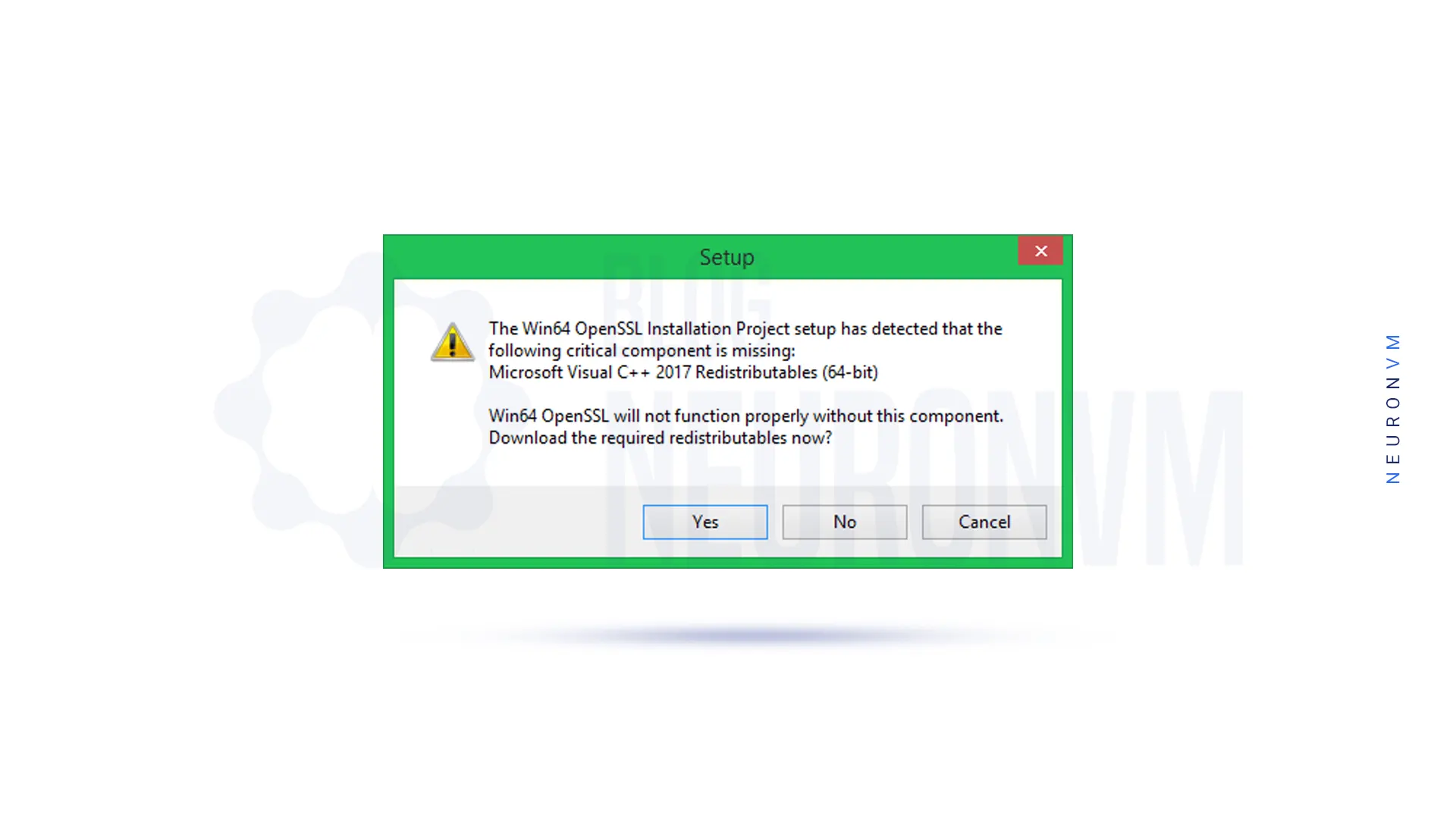
Note: If your system does not have Microsoft Visual++, the installer will display the following message. Because OpenSSL requires Microsoft Visual C++ to be installed on your system.
You should Click ”Yes” to download and install the required Microsoft Visual C++ package on your system:
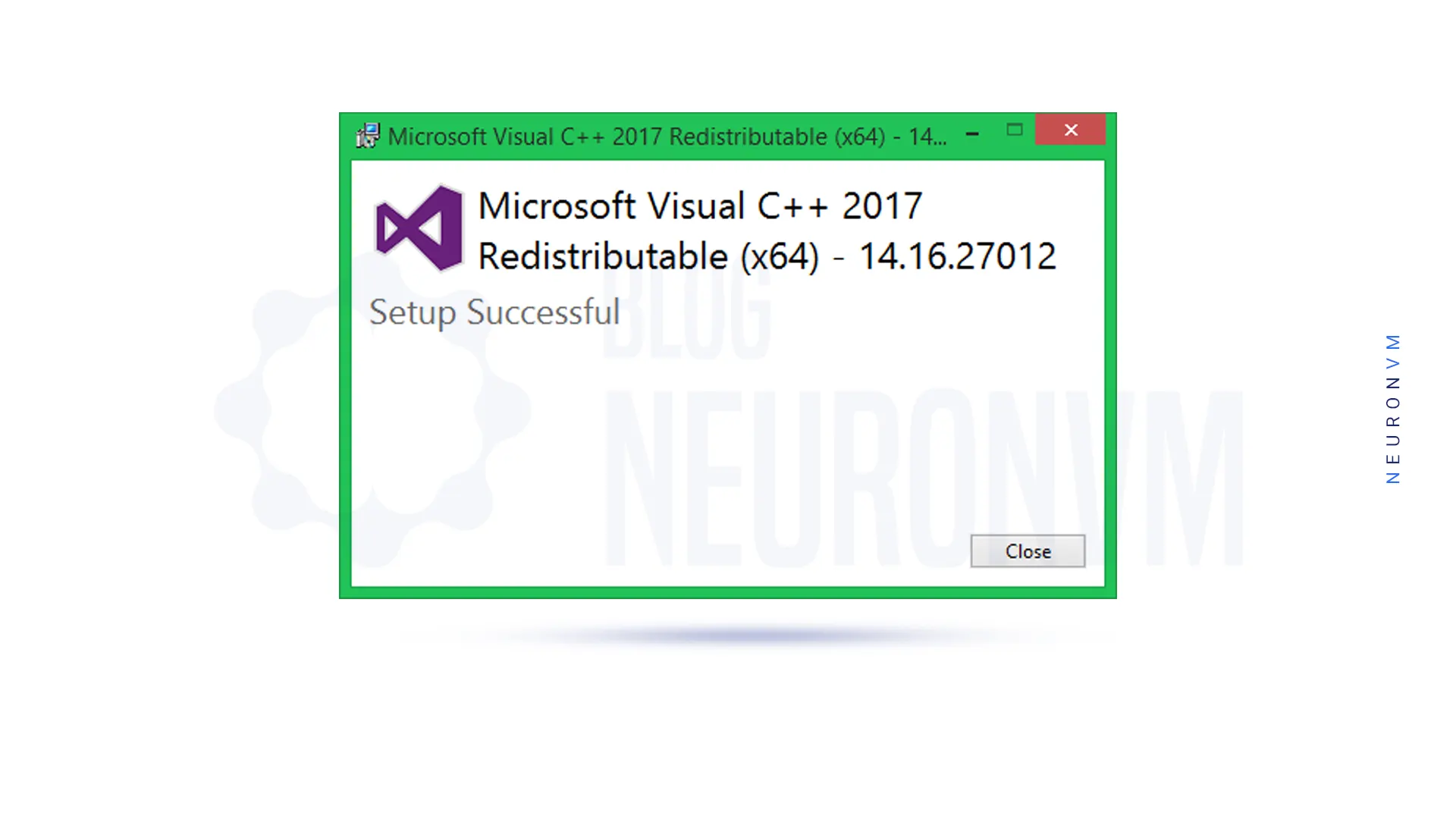
You will see that Microsoft Visual++ installs successfully:
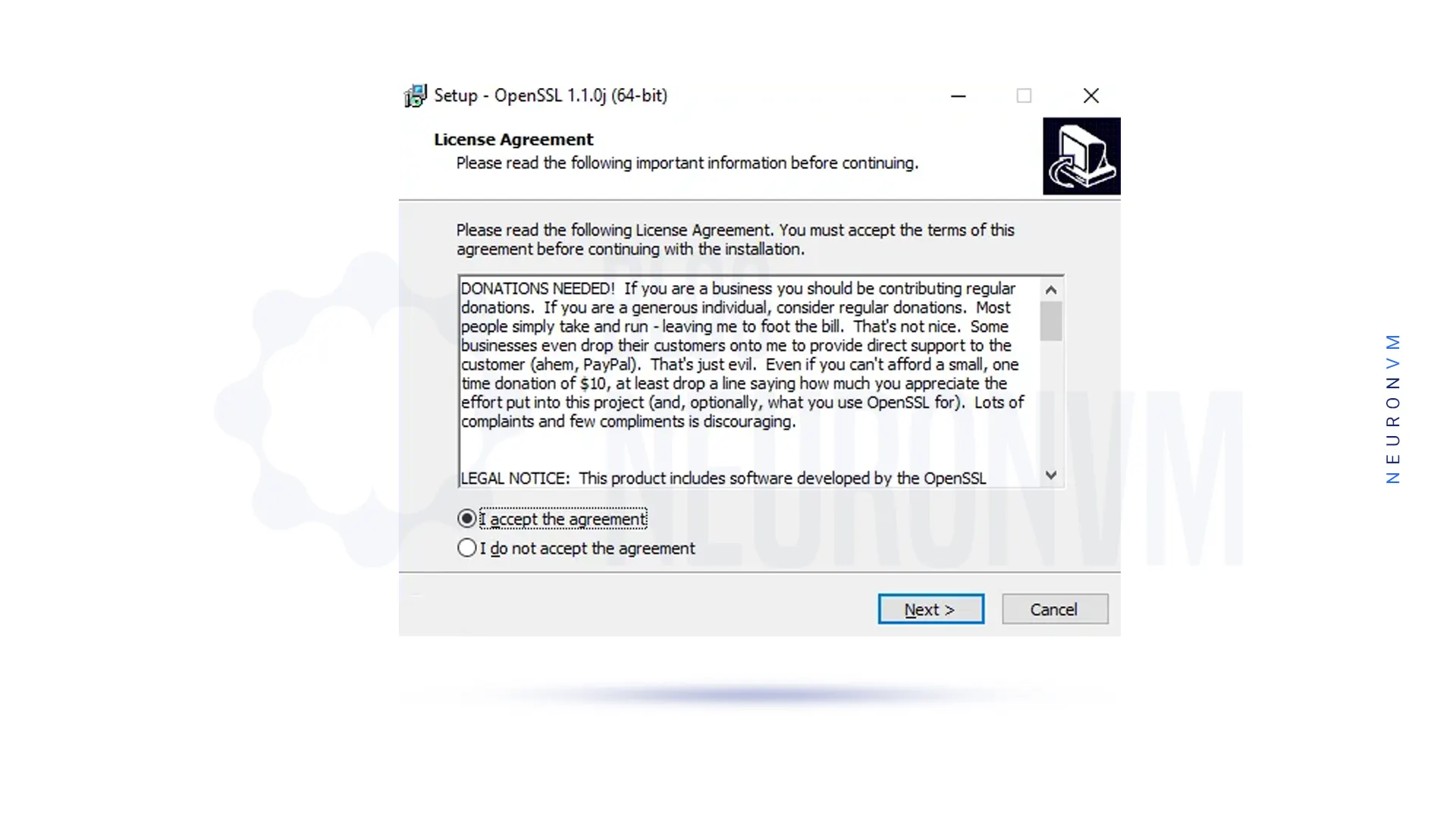
Now you should accept the Software License Agreement and click ”Next”:
Next, you should select the destination folder, Where OpenSSL will install:
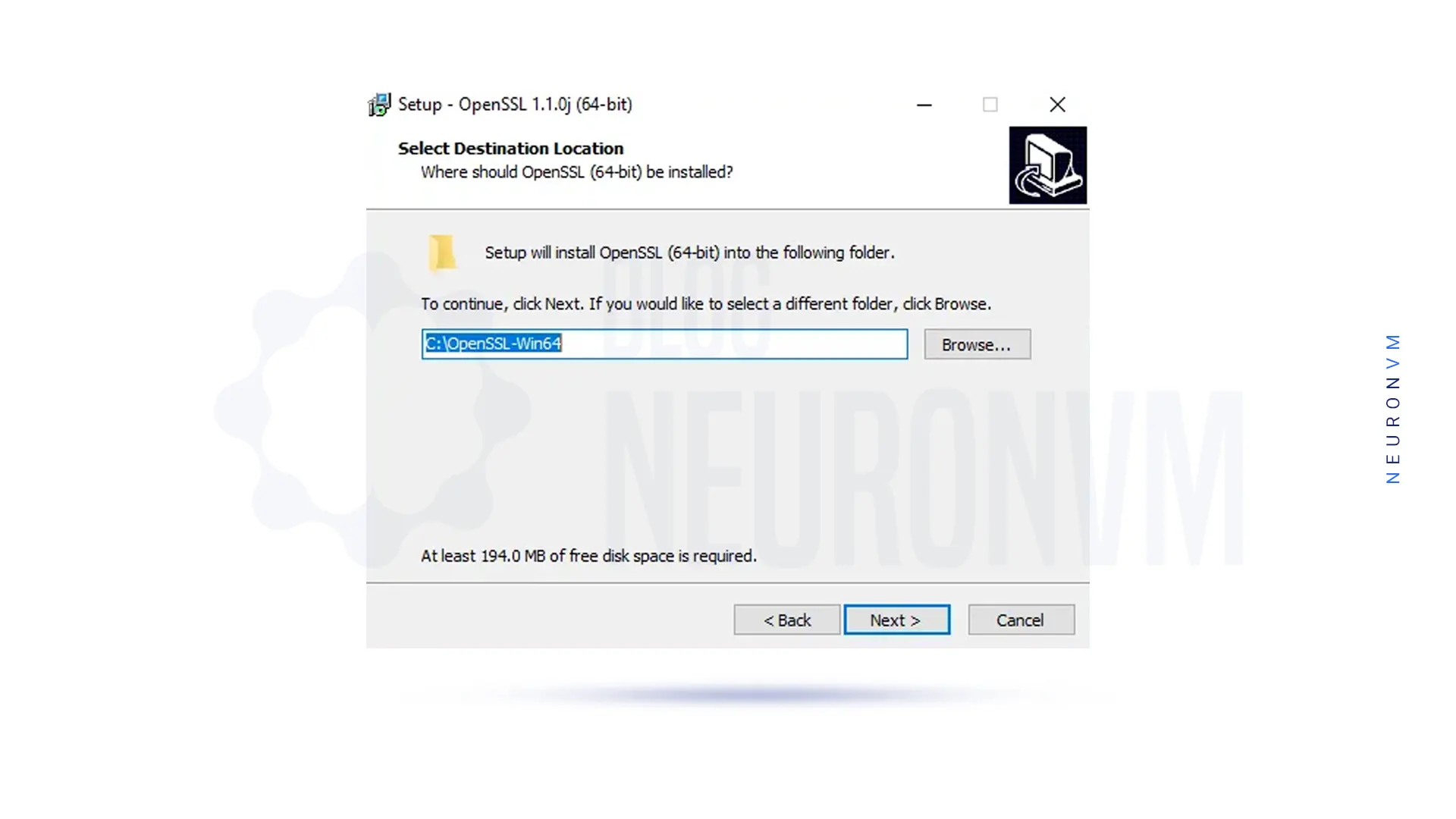
Also, you can select the directory for the Application shortcut:
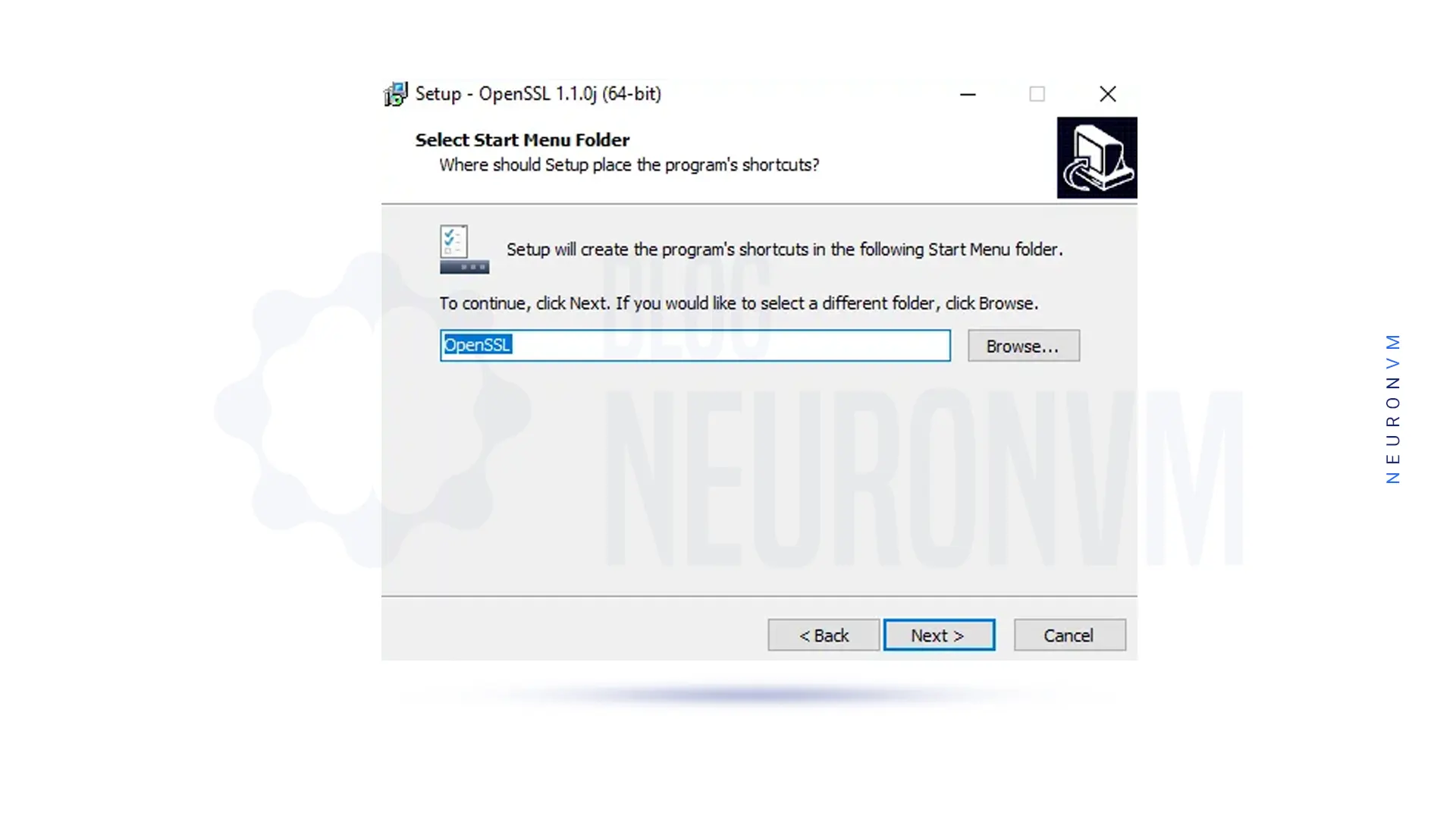
In the next step, you should select additional tasks to perform:
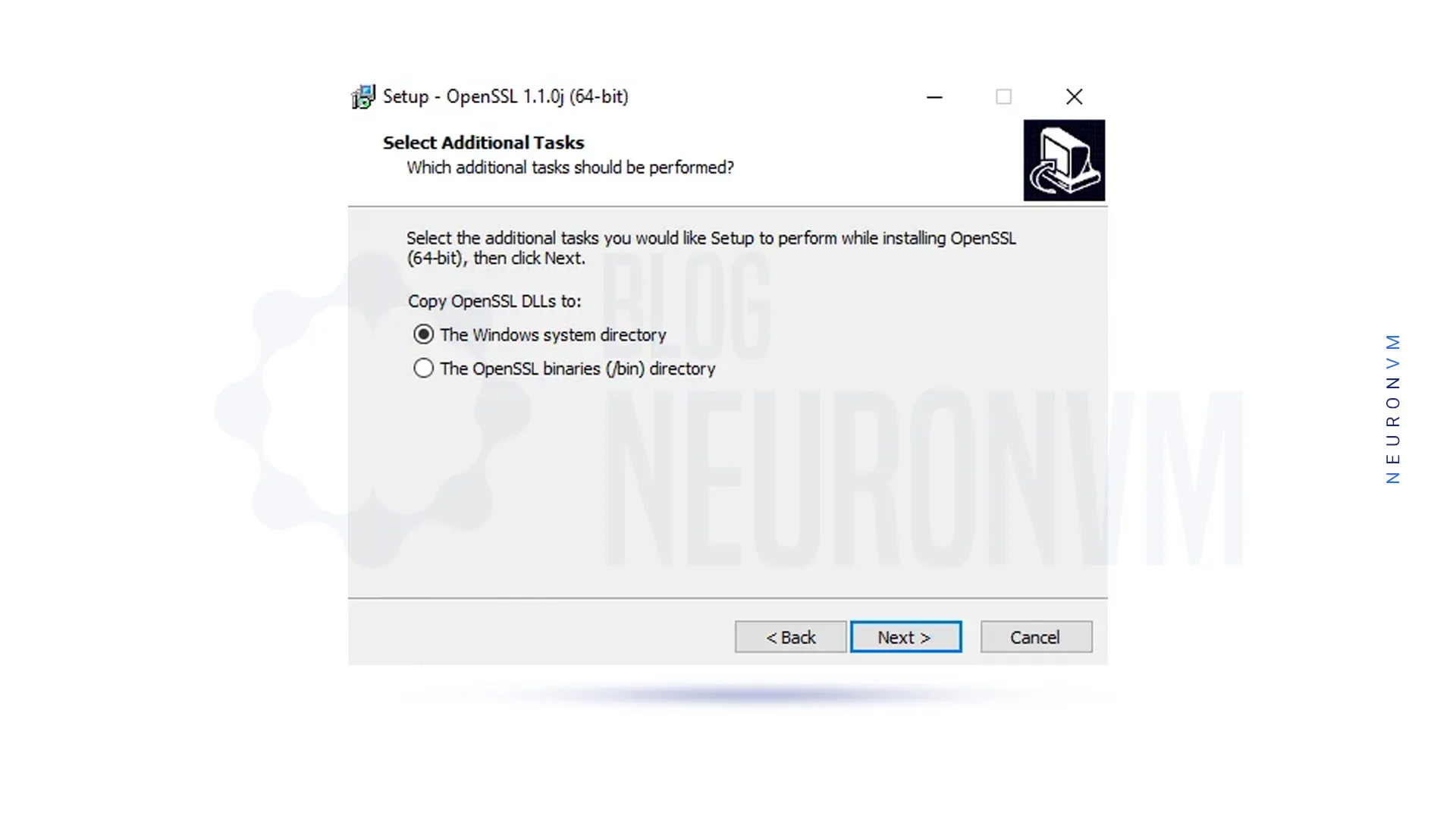
You must click ”Install” to start the installation of OpenSSL on Windows Server 2016:
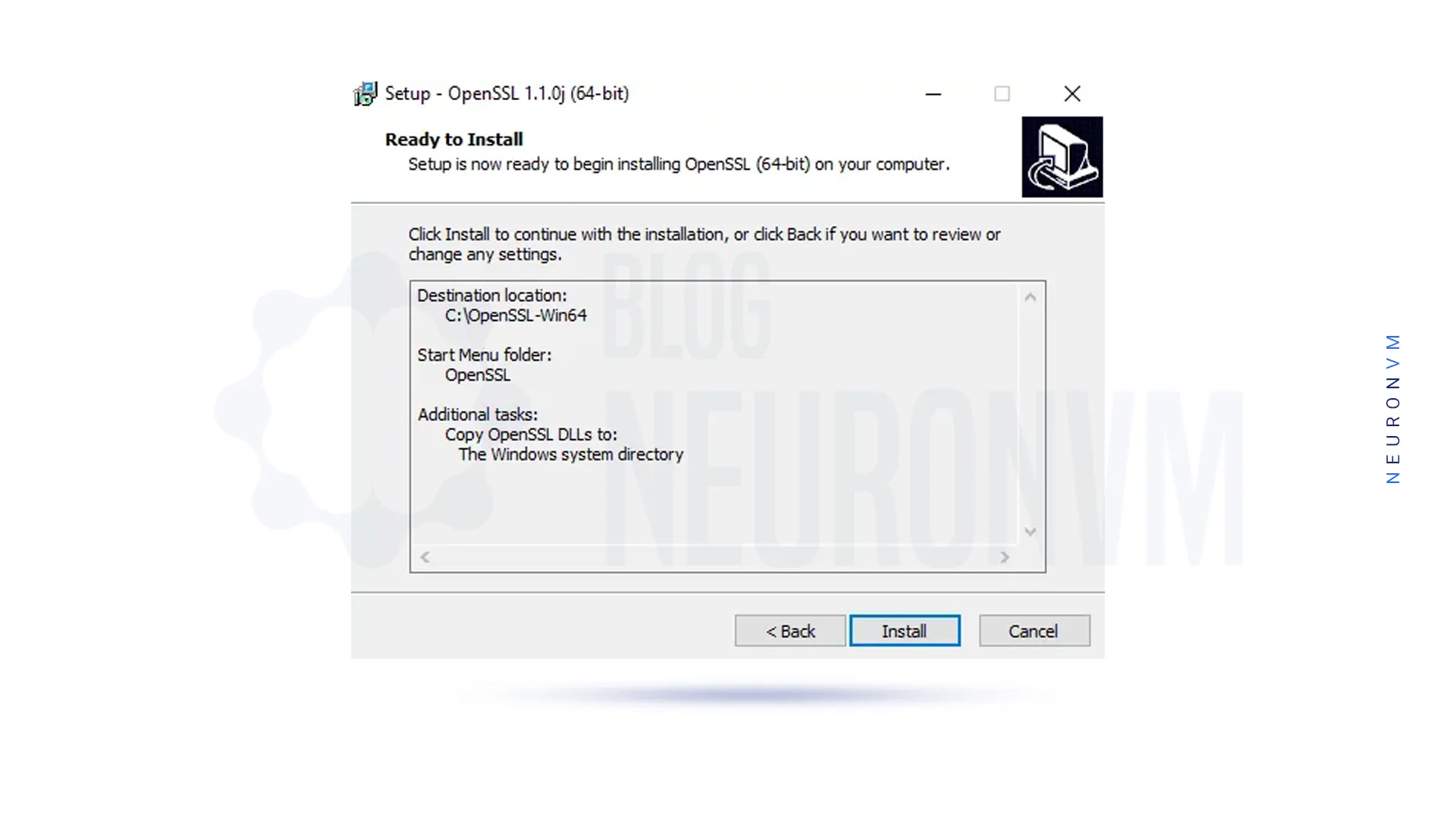
After the installation is complete, click ”Finish”:
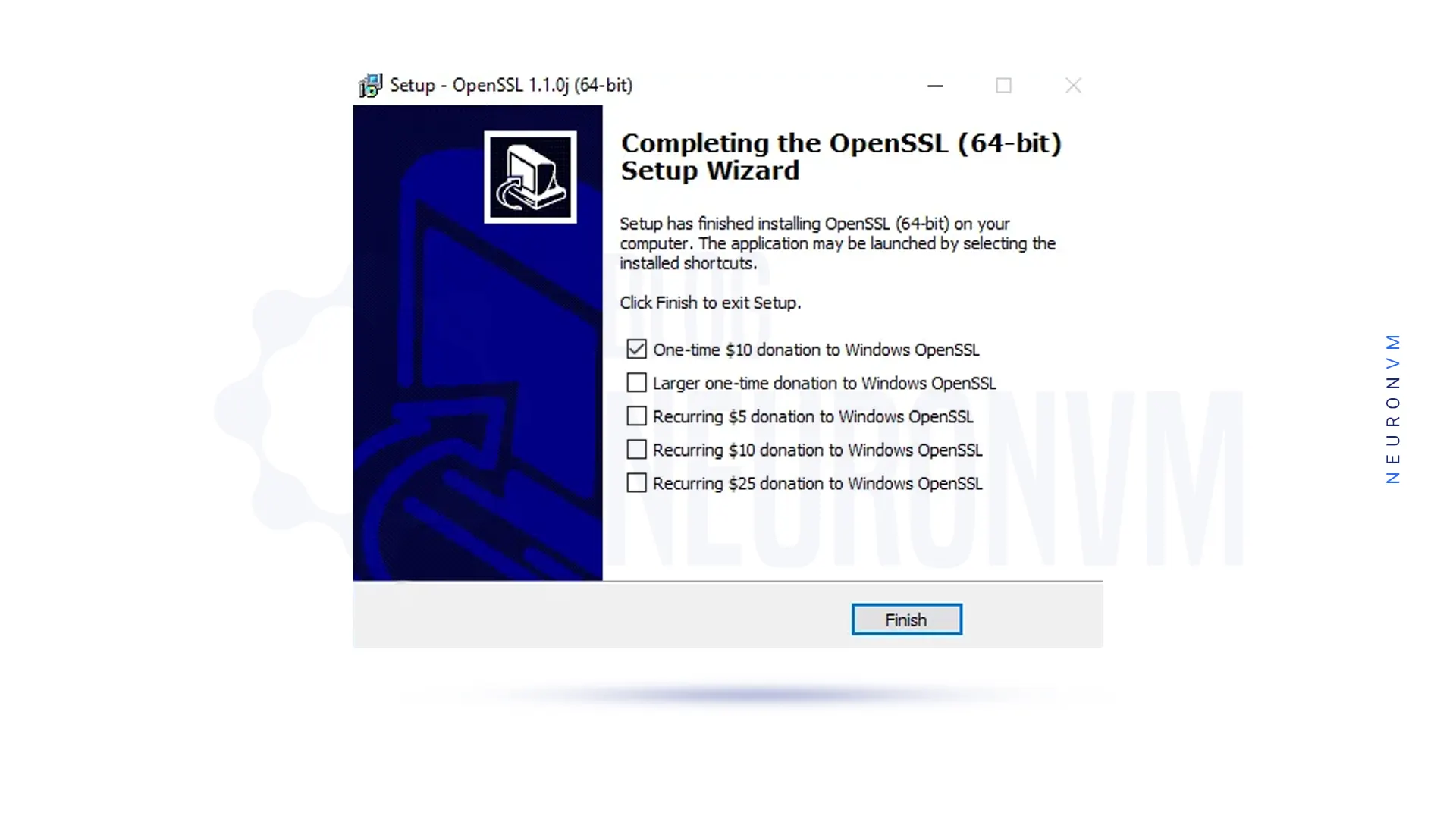
For OpenSSL to work properly on your system, you need to configure environment variables. After you have successfully installed OpenSSL, we will start it in this section. You are now ready to use OpenSSL on RDP 2016 to generate certificates. Export the OPENSSL_CONF file to get started using the following command:
set OPENSSL_CONF=C:\OpenSSL-Win64\bin\openssl.cfg
Note: If your system is 32-bit, you can type and run the OpenSSL-Win32 command in the above command instead of OpenSSL-Win64.
Finally, you can create a test SSL certificate to verify your installation. To do this you can use the following command:
openssl.exe req -new -nodes -keyout server.key -out server.csr -newkey rsa:2048
Now you can use OpenSSL on RDP 2016 to generate certificates.
Setting up OpenSSL on RDP 2016 is essential for securing your network communication and protecting sensitive data from unauthorized access. By following the steps outlined in this guide, you can successfully configure OpenSSL on your server and ensure a secure and encrypted connection between clients and servers. Remember to regularly update OpenSSL and your SSL certificates to maintain the highest level of security for your RDP 2016 environment.
How useful was this post?
Click on a star to rate it!
Average rating 5 / 5. Vote count: 2
No votes so far! Be the first to rate this post.
 Tags
Tags

PowerShell is a powerful scripting language and command-line shell that allows automation and manage...



 Tags
Tags

You've probably noticed by now that URLs on the Internet start with the two prefixes HTTP and H...



 Tags
Tags
What is your opinion about this Blog?
openssl genrsa -out private.key 2048 openssl req -new -key private.key -out csr.csr openssl x509 -req -days 365 -in csr.csr -signkey private.key -out certificate.crt openssl genpkey -algorithm RSA -out private_key.pem openssl rsa -pubout -in private_key.pem -out public_key.pem openssl rsautl -encrypt -pubin -inkey public_key.pem -in input_file.txt -out encrypted_file.txt openssl rsautl -decrypt -inkey private_key.pem -in encrypted_file.txt -out decrypted_file.txtopenssl version







